Today I’ll be bringing you through a short walkthrough on how to unpack Malware (in UPX) . It is important that we look at the bare bones of the executable and it’s intended functionality to understand the goals of the Malware author. Other reasons why we want to unpack Malware before completing our analysis are:
>
- Identification: Malware can be disguised in various ways, such as through obfuscation, encryption, or compression. Unpacking the malware can reveal its true nature and make it easier to identify and analyze.
- Analysis: Once the malware has been unpacked, it can be analyzed to determine its behavior, capabilities, and potential impact. This information can be used to develop countermeasures, such as antivirus signatures or intrusion detection rules.
- Reverse Engineering: Unpacking malware can provide insights into how it was created and the techniques used by its authors. This knowledge can be used to improve security practices and develop new defensive strategies.
- Prevention: Unpacking malware can also help in preventing future attacks by identifying patterns and common features in malicious code, which can be used to develop proactive defenses.
Before we start unpacking, there are a few things you will want to do. First off NEVER try this on your host computer. Always use a virtual machine with the host only adapter enabled as the networking protocol and always have a snapshot of a clean VM so you can Nuke the infected one once complete. Secondly, you will want to use a couple handy tools like TridNet or Exepeinfo. These tools will first help us Identify if the malware is a executable and if it is packed or not which is essential in determining what tools we will use to Unpack the malware for further analysis.

Unzip your malware file > Drag and drop it onto the TridNet GUI
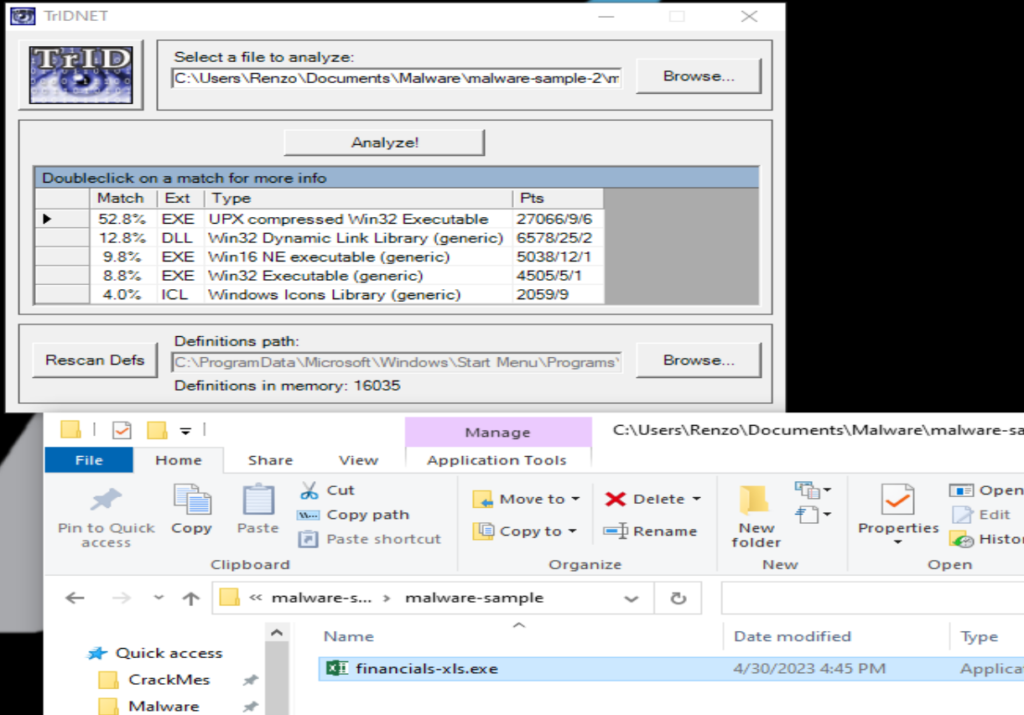
Now, from this view we can still tell that it is a Windows32 executable. However, 52% of the file is UPX compressed which means our detections may not catch certain obfuscated code especially if there isn’t already a signature already out there for this particular malware. The compression can make it more difficult for antivirus software to detect the malware, as the compressed code may not match known malware signatures. In addition, UPX can be used to pack multiple pieces of malware into a single file, making it harder for security researchers to analyze and identify the individual components.
>
Now let’s unpack the malware. You will need to download a UPX unpacker from github. This particular one is a CLI based unpacker so let’s get started. **IMPORTANT** Since this is a 32bit program you will need the 32bit unpacker for your OS or it will not unpack.
I’m also going to include a snapshot of the PE file placed into PE studio before the malware is unpacked so that we can observe the differences. We can see that although the malware is packed, it still gives us quite a bit of information on it but just how much are we missing out on?

Now let’s go ahead and navigate to our directory with the upx utility and our execuatble. We will be using the following command ‘ upx -d -o financialsunpacked.exe financials-xls.exe ‘ to point it to the file desired for unpacking and then renaming it in the same directory.
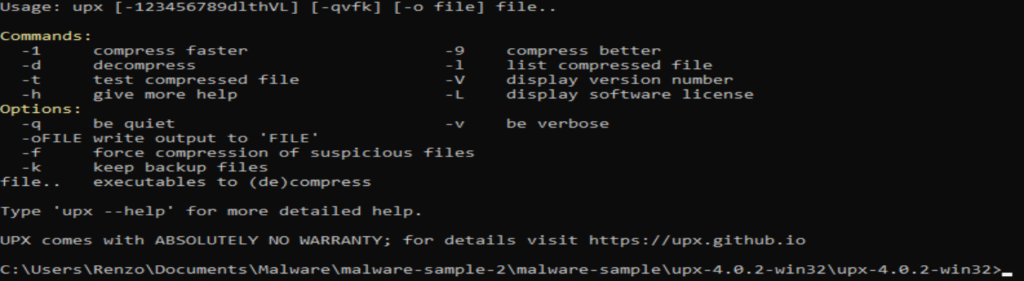
If successful you will see the following prompt.
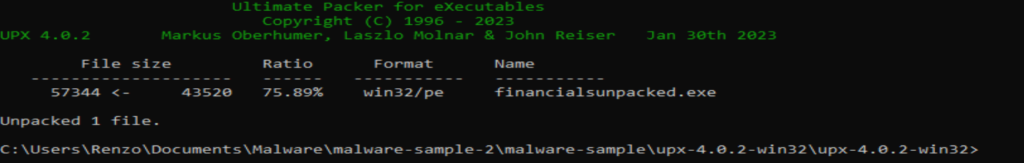
Now with the unpacked file, trid tells us a lot more information. We can see that it is written in C++ and it’s using a known malware crypter called “Yoda’s” Crypter.
This is a popular crypter tool that is freely available online. It can be used to encrypt various types of malicious code, including Trojans, keyloggers, and backdoors, and it is known for its ability to evade detection by many antivirus programs.
The crypter works by encrypting the malicious code and embedding it into a benign executable file, such as a legitimate software application or game. When the victim runs the file, the malicious code is decrypted and executed on the victim’s system, without raising any alarms from security software.

>
Pivoting back to PE Studio, lets compare.
Before (left) and after (right).
Just by unpacking the malware we were able to help our computer make sense of the program by deobfuscating the program. We can see that the unpacked program is doing all sorts of things a Excel file shouldn’t be doing like adding registry keys, writing files, deleting files, getting the desktop window and other malicious things.
We can also see at the bottom it is hard coded to send a get request to download another file from the bravesentry[.]com domain which is most likely a C2 and second stage loader.

Thanks for reading my very brief introduction to unpacking malware and why it’s important to do so to get the most out of your detection tools.

Comments are closed