With Azure Bastion, users can securely access their VMs using a web-based console over SSL-encrypted HTTPS connections, without the need for a public IP address, VPN, or remote desktop client. This simplifies remote access and eliminates the need for a jumpbox or other intermediate hosts, reducing the attack surface and improving security. Azure Bastion integrates with Azure Active Directory (Azure AD) for user authentication and role-based access control (RBAC) for fine-grained access management.
In this short demonstration I will be showing you how this can be set up on my Azure tenant.
All credit goes out to Cloud Academy for providing this interactive lab
First let’s navigate to the Bastions service. Select Bastions
Once on the Bastions host main page, select create Bastion
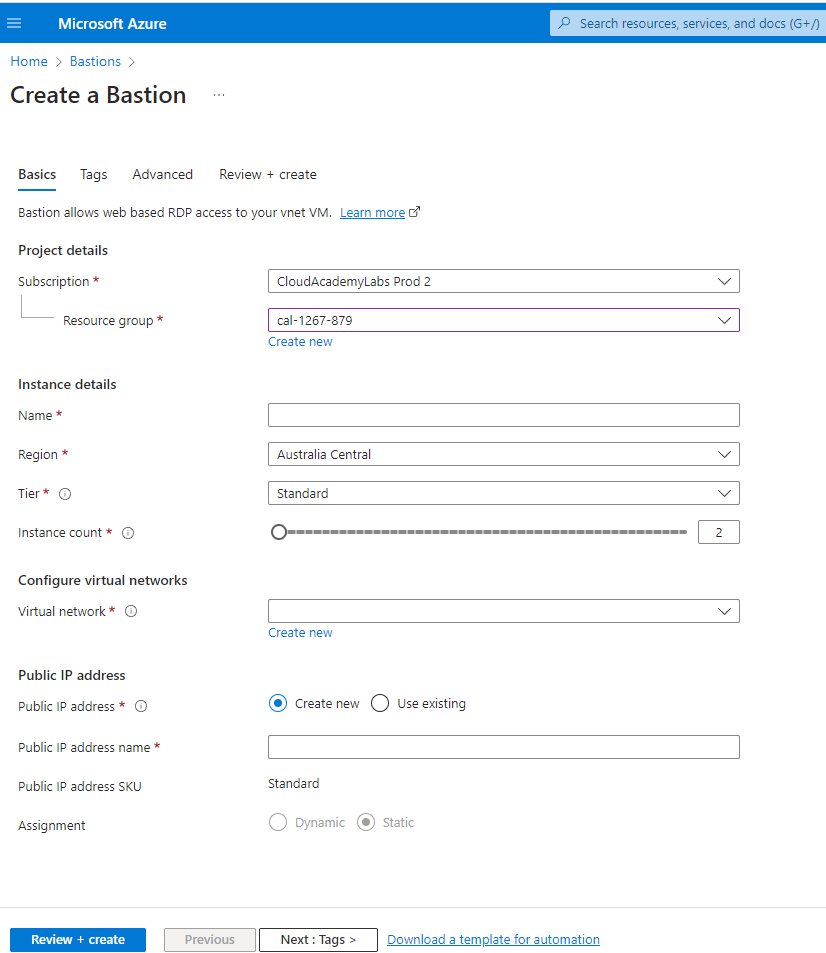
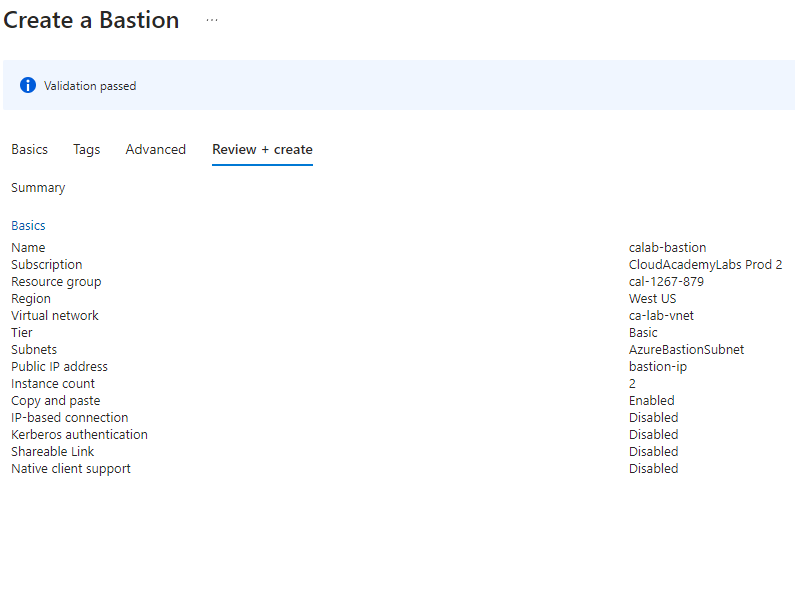
On this page, you”ll need to select the proper subscription, resource group, virtual network that the VMs are hosted on and lastly the tier of Bastion you are using. Be sure to select the proper tier or the Bastion host will not provision.
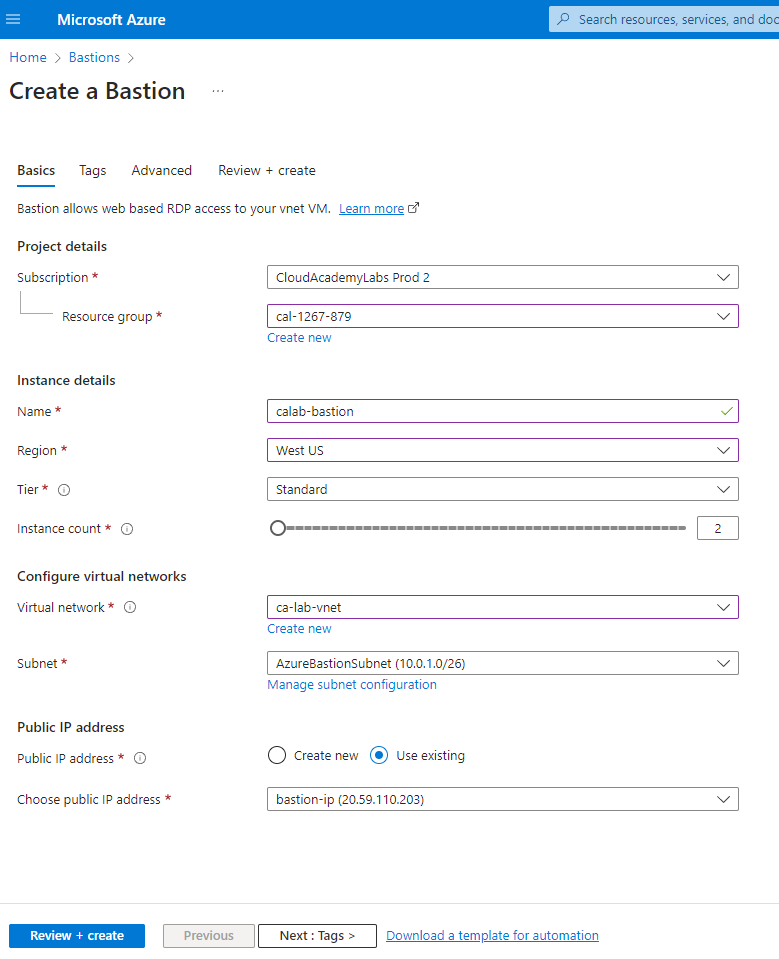
Your final results should look something like this below.
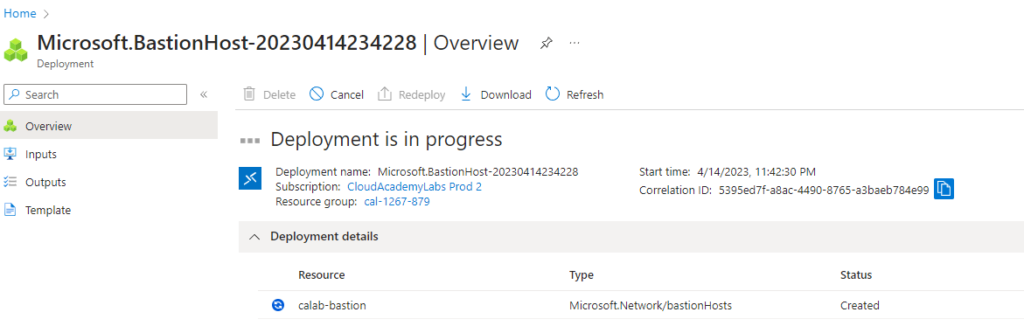
Wait for deployment to finish initializing this could take up to five minutes.
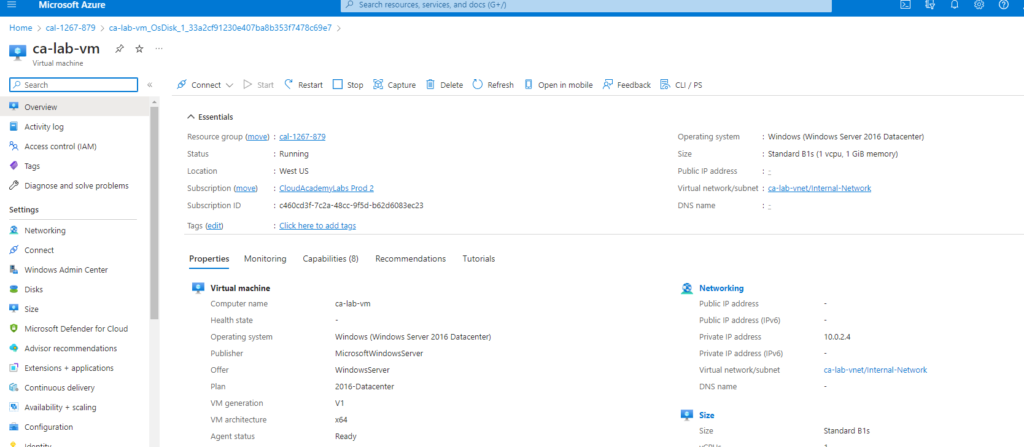
After initializing is finished, click connect
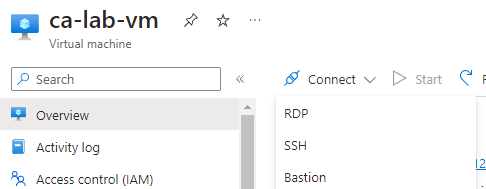
Select Bastion, since this is the method we will be using to connect to the VM.
Enter the credentials
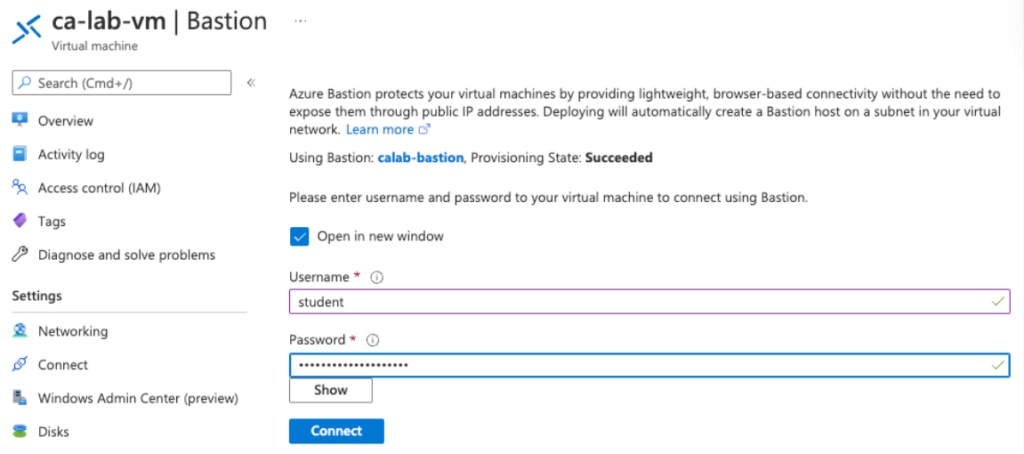
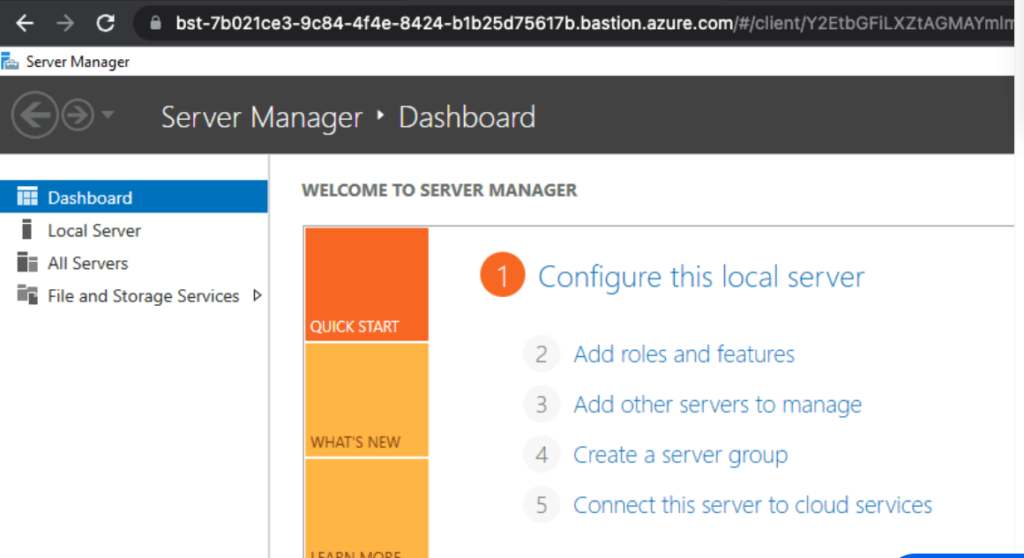
You are now connected to Bastion over SSL to the virtual machines.

Comments are closed