In this project I will be demonstrating my ability to utilize Splunk by configuring the event manager, sigma rules, and implementing alerts
This is the Splunk Enterprise homepage. I am currently using the “tryhackme” platform to access their virtual machine in the cloud. Let’s go ahead and get started by selecting Add Data
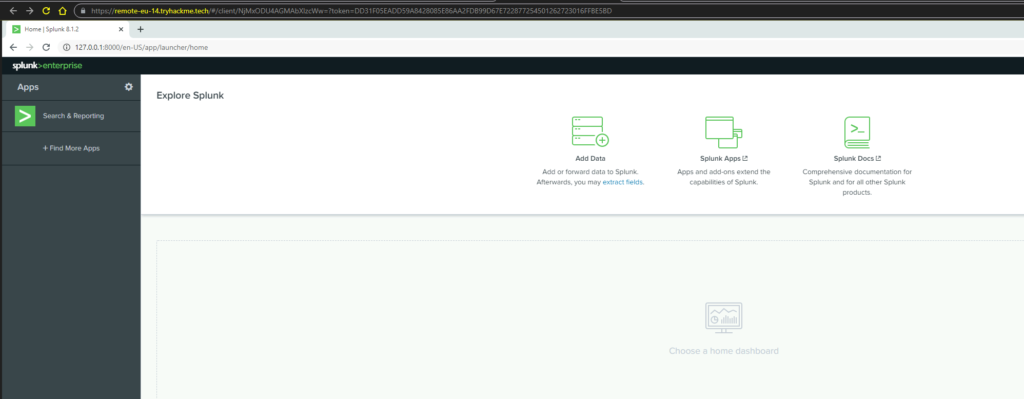
From this page I selected the monitor option in order to configure the instance we will be using
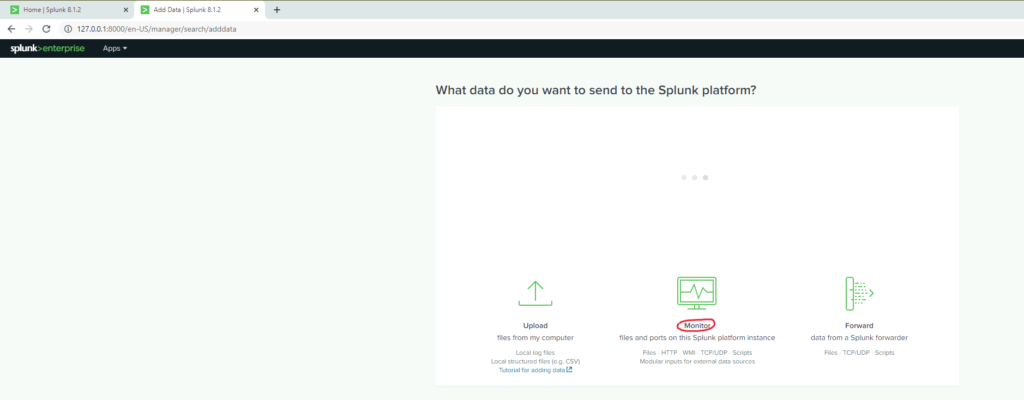
Here I am capable of monitoring various types of log files along with systems health performance.
I selected Local Event Logs since I am using a pre-configured lab that has event logs downloaded on the local machine already
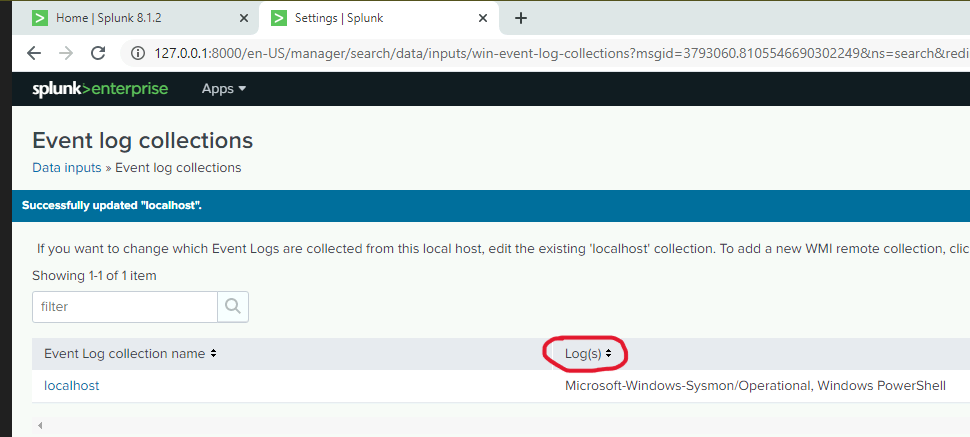
I am specifically looking for PowerShell and Sysmon logs but I noticed that they are not listed in the “Available items” drop down menu. To fetch the logs I need I will navigate over to the Settings > Data Inputs
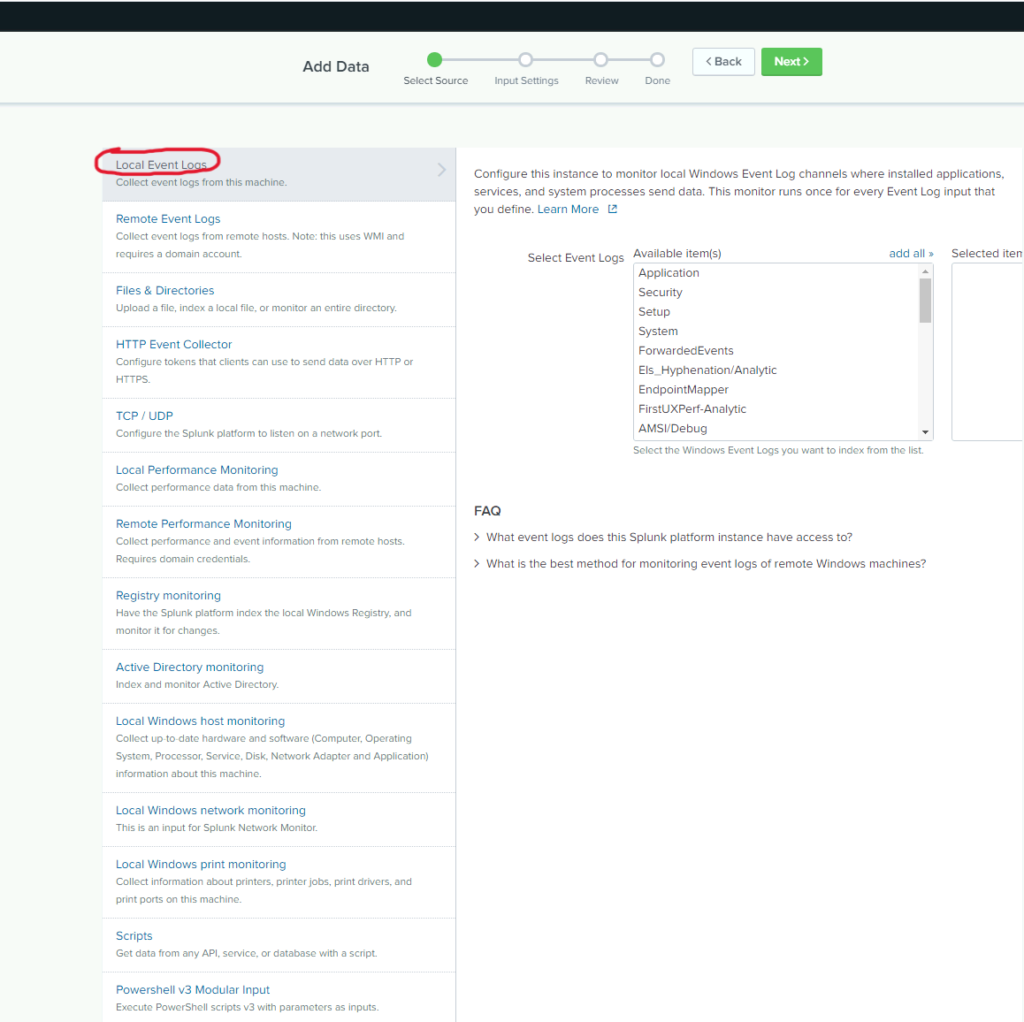
As you can see, there are a plethora of logs we can choose from now. I suggest using the CTRL + F keys to search quickly for the types of logs you may be searching for.
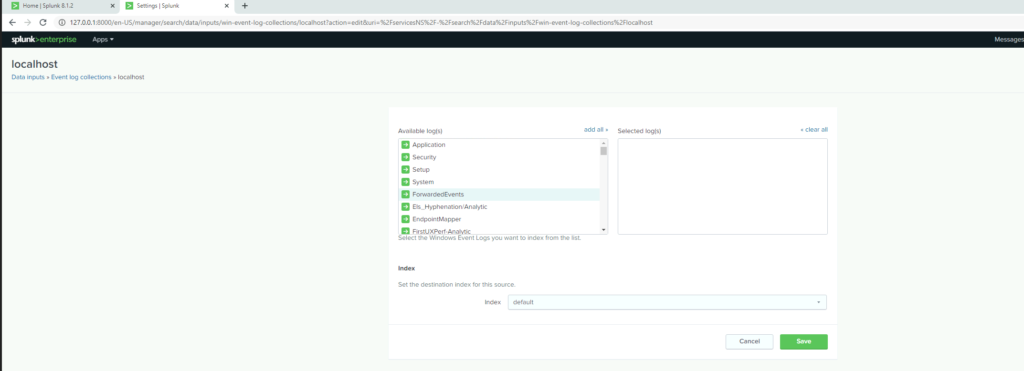
The Event log collections has successfully been configured to my needs, now I will upload the the log files from the local machine and run some basic search filters
What you are looking at here is essentially just a default search that tells us how many total events we have in this instance

If I would like to specify a certain source or source type I would just specify that in the spacebar like so
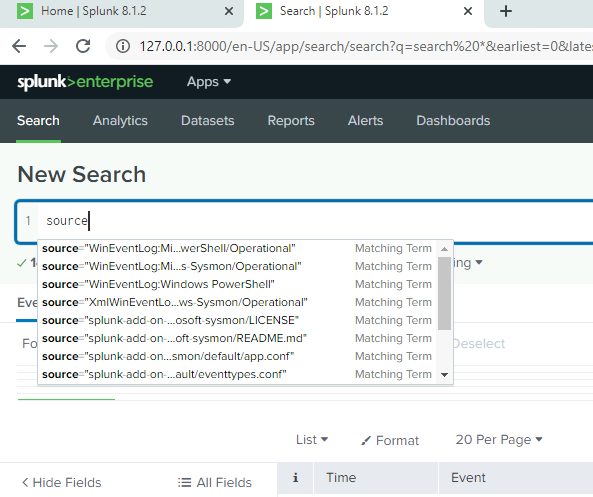
Now for a more practical example of how to use the search feature, we are going to query some failed password attempts by entering * "failed password events for sneezy"
This reveals some pretty alarming information to me. There are 84 failed password attempts from various different types of IP addresses.

Sigma Rules – Threat Detection Sharing
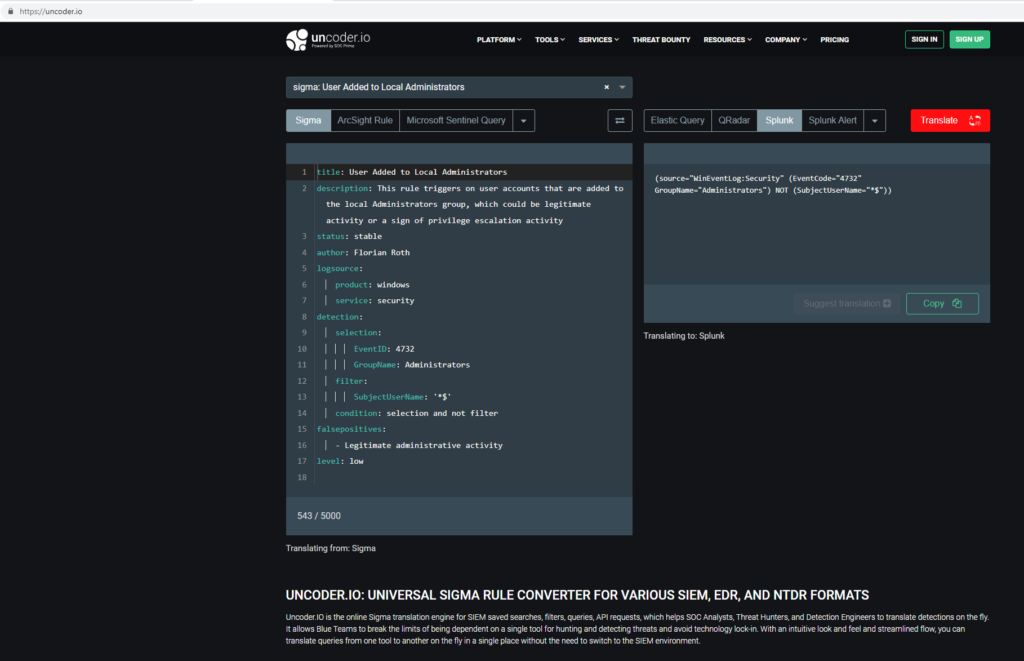
Lets talk about Sigma rules. The platform uncoder.io allows its users to translate rulesets from one SIEM platform to another. Sigma rules themselves are essentially just baseline rulesets that all of the SIEM’s have in common. This is highly effective when sharing detection methods and eliminates vendor lock-in
As demonstrated below, the sigma rule is selected and then translated into whichever SIEM query language you need to search the log files

No responses yet