Nessus is one of the most prominent vulnerability scanners in the industry at this time. In this lab, I will be conducting a basic vulnerability scan against a VM with an old FireFox version installed on the machine. Nessus is fairly simple scanner to use so this will be a rather short demonstration. Let’s get right to the meat and potatoes.
Here we went ahead and entered the IP address into Nessus to run a host discovery.

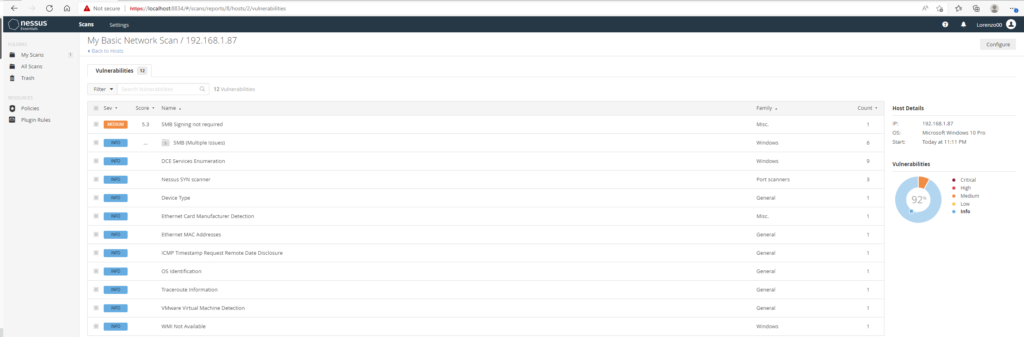
Next we are going to run a basic network scan on our host (uncredentialed). There are 5 threat levels Nessus uses : info, low, medium, high and critical. The VM in this project has one medium level threat. By clicking on it you can see more information about the vulnerability and how to remediate it if you wish to do so.
Certain vulnerabilities will not be addressed as risk acceptance varies from organization to organization.
Here we are about to install a old version of FireFox and see what Nessus uncovers for us. I also enabled a CREDENTIALED scan. This can be done by going to the configure tab and entering the username and password of the machine. This will allow Nessus access to the registry on the VM which will allow for a more thorough scan.
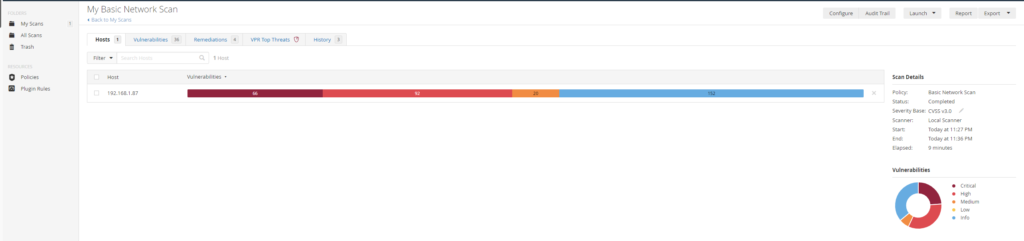
Wow! Look at all of those new vulnerabilities, let’s see where most of them are from.
As expected, we have multiple critical vulnerabilities from the version of FireFox we installed on the VM. This can be easily remediated by updating FireFox and then scanning the machine again to ensure that there are not anymore vulnerabilities.


No responses yet