What is SMB?
SMB – Server Message Block Protocol – is a client-server communication protocol used for sharing access to files, printers, serial ports and other resources on a network. [source]
Servers make file systems and other resources available to clients on the network. Client computers may have their own hard disks, but they also want access to the shared file systems and printers on the servers.
The SMB protocol is known as a response-request protocol, meaning that it transmits multiple messages between the client and server to establish a connection.
Now lets get started!
The key tool we will be using in this project will be “Enum4Linux”. This tool is used specifcally for enumerating SMB shares on both Windows and Linux systems. This is installed by default on Parrot or Kali Linux but if you need to install it you can do so from Github.
https://github.com/CiscoCXSecurity/enum4linux
First we need to enumerate to gather some information on our target machine, in the photo provided you can see that we have identified three ports are open using our NMAP scan. [nmap -sV IP]
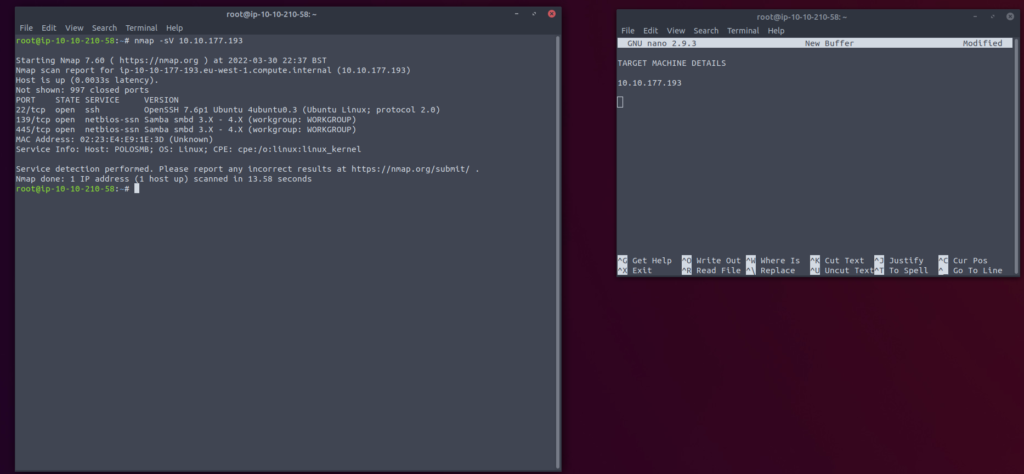
We can tell from this scan that SMB is running over ports 139/445 over TCP
Now lets run out Enum4Linux command and see if we can sniff a sharelist and any other possible useful information.
After running the enum4linux -a command we found out that the workgroup name is “WORKGROUP”. We also learned that the name of the machine is “POLOSMB” and the sharelist populated as well with an interesting directory that we are interested in looking further into called “profiles”.
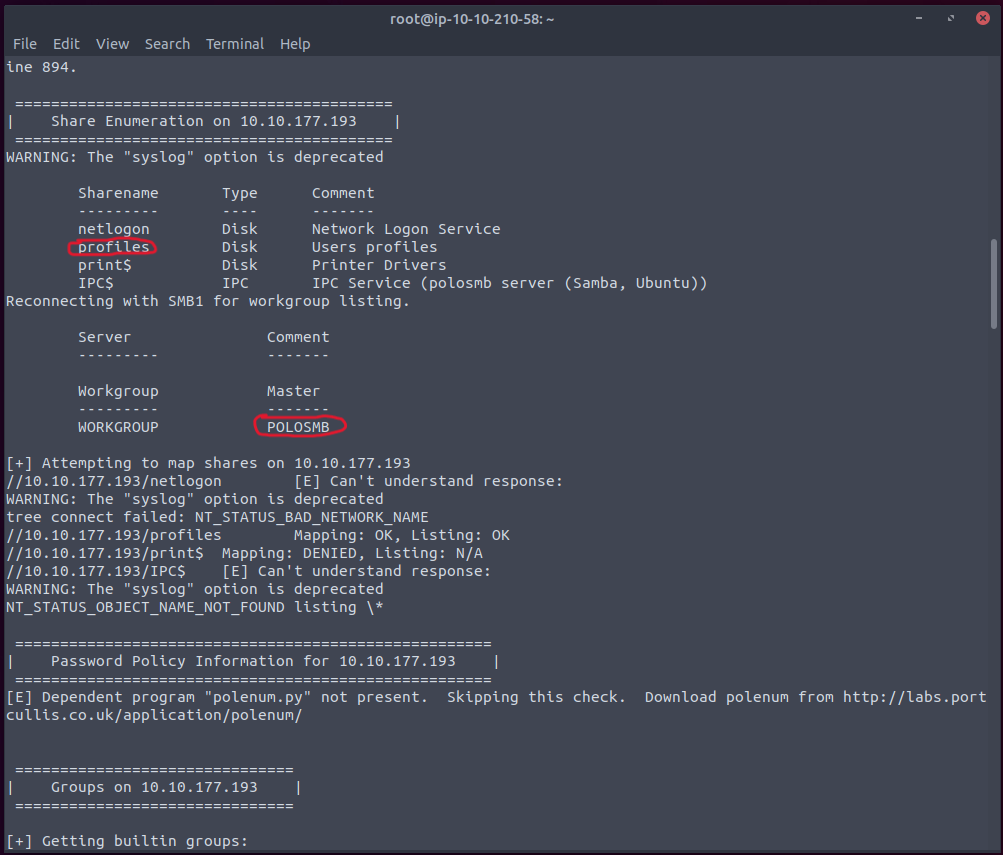

There are other vulnerabilities that can actually allow remote code execution by exploiting SMB but it’s said that you are much more likely to find a misconfiguration in the system. In this case we’re doing just that, we’re exploiting anonymous SMB share access which is a common misconfiguration that will lead us to a shell.
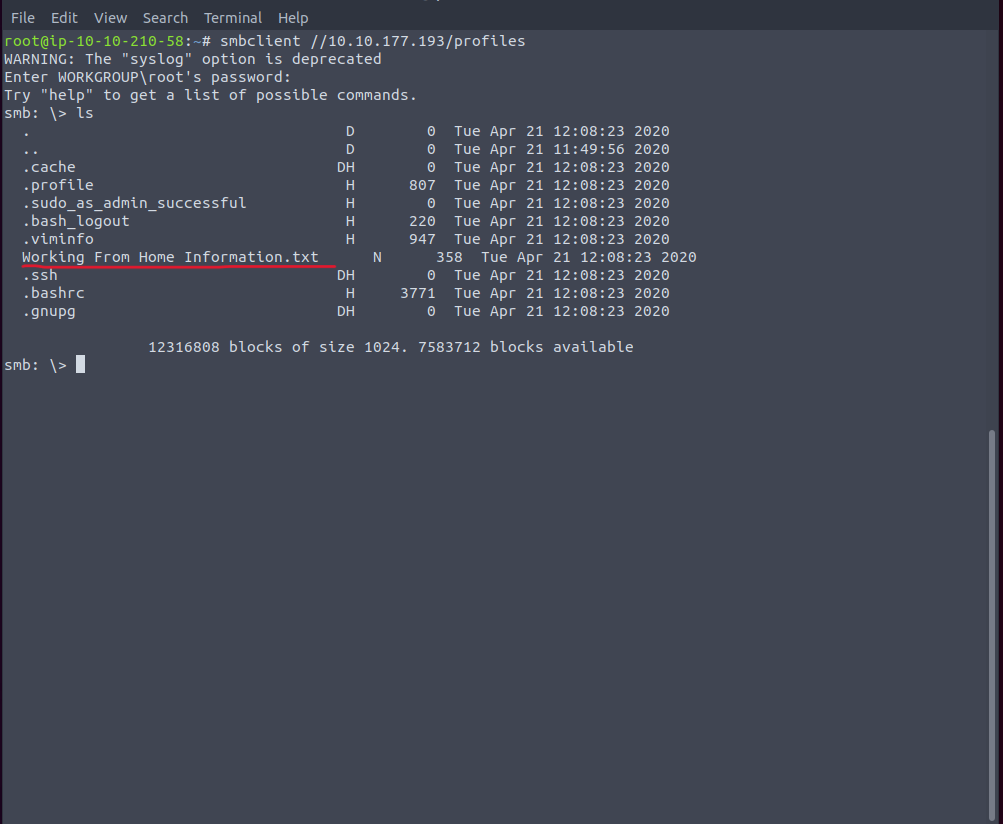
In the photo above you can see we used thesmbclient //[IP]/profiles command and we were prompted with a password entry. We used anonymous and were able to get in. Now using the ls command we were able to get a list of directories within the SMB client.
We took a look around and exfiltrated the “Working From Home Information.txt” file to see what information we could gather.

Looks like we will hit the jackpot if we can figure out John’s login credentials. We can tell from the message that he now has full SSH access into the main server and we have also recovered his first and last name which could be his username or profile folder name.

No responses yet